本日、私たちはテストネットにデプロイしました。量子およびAI耐性トランザクションをお楽しみ …
本日、私たちはテストネットにデプロイしました。量子およびAI耐性トランザクションをお楽しみください
SORA Integrate Wallet -> getkeyentangle()
[SORA] junkhdd.com / fromhddtossd.com / iuec.co.jp / web3dubai.io

本日、私たちはテストネットにデプロイしました。量子およびAI耐性トランザクションをお楽しみ …

Today, we deployed on the testnet. Please enj …
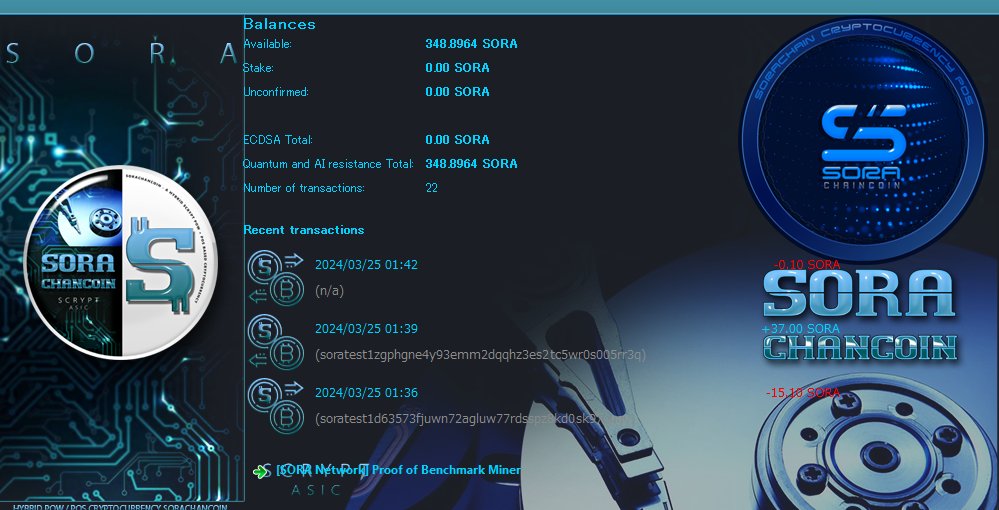
ECDSAで見つかったSORAをクリック一つで量子&AI耐性へ移行するトランザクションを生 …

We have successfully introduced a feature tha …

本日、CoinTelegraphの記事で、サイドチャネル攻撃によりAppleのMシリーズチ …

Today, A CoinTelegraph article mentioned the …
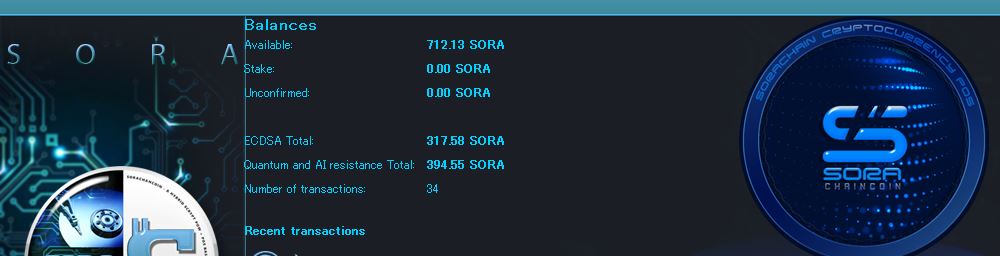
画像をご覧ください。残高表示は「ECDSA合計」と「量子およびAI耐性合計」に分かれていま …

Please look at the image. The balance display …
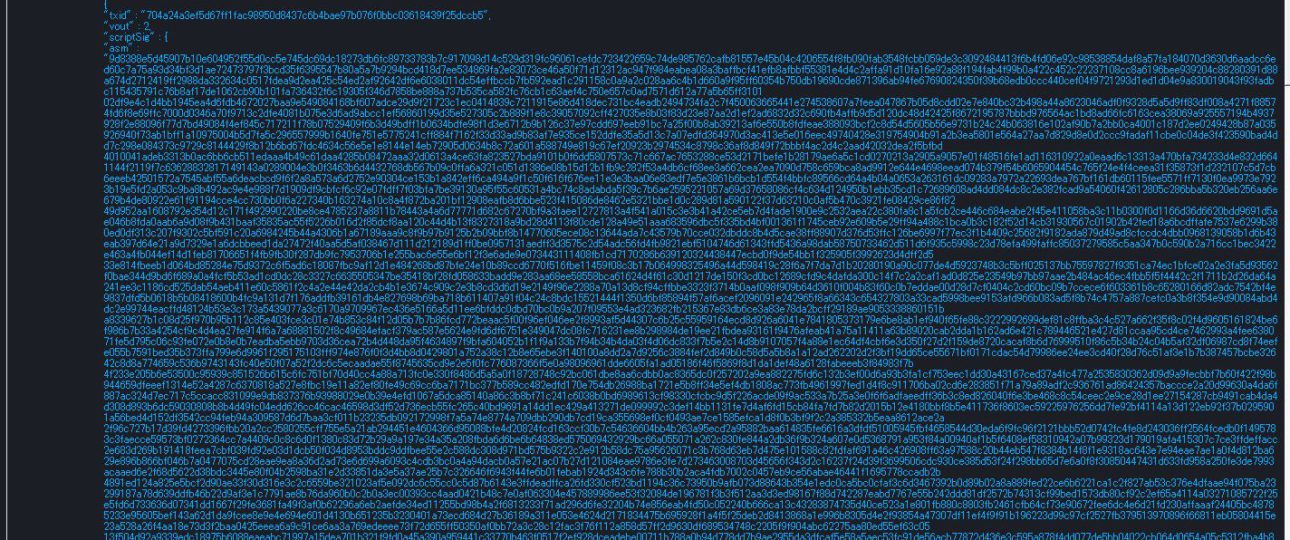
私たちはSORA L1テストネット上でのトランザクション内容を検討しています。script …

We are examining the transaction contents on …

量子およびAI耐性トランザクションは順調に進んでおり、ステーキングが確認され次第、メインネ …

Well, the quantum & AI-resistant transact …
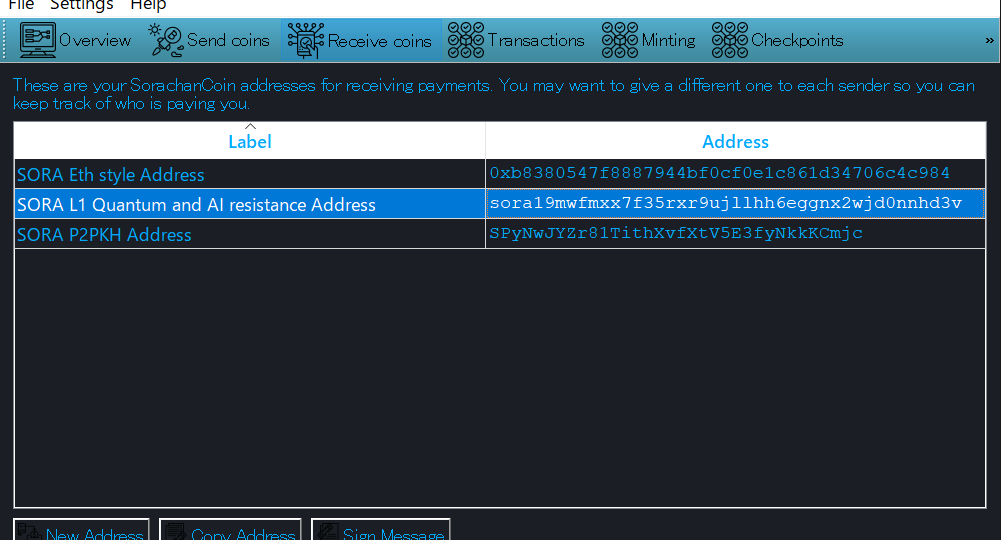
実装は順調に進んでいます。現在、3種類のキーを取り扱うことになります。画像で、上から順に、 …

The implementation is progressing smoothly. W …

量子&AI耐性の実装に向けて急速に進展しています。 scriptPubKeyの構造が決定し …